
IoT and Embedded Systems
Scalable Preventative Security
A World Increasingly Connected, with IoT/Embedded Systems. The sheer breadth and complexity is staggering, and a massive endeavor to secure and support. Their Artificial Intelligence (AI) driven approach helps mitigate risks - in medical devices, security systems, cars, etc. - for better business outcomes.
Protecting Near-Infinite Points of Vulnerability
Medical Device Security Assessment
Cylance identify and evaluate security issues associated with medical devices - threats and vulnerabilities that may impact patient privacy and safety. By securing devices you can ensure their availability, integrity and reliability.
Embedded System Security Assessment
Their team test the components which are most likely to be exploited and represent the greatest system impact. By identifying potential security risks in embedded devices, they can be secured and protected from the risk of cyberattack.
Vehicle Security Assessment
Aided by advanced AI, we identify how vulnerabilities can be introduced, map the attack surface of elements and components, and conduct threat modeling/assessment of complete vehicle systems.
Med Secure Assessment Framework (MSAF)
Identify gaps in clinical information security programs by evaluating people, processes, and tech associated with the defense of critical patient care systems – like medical devices or laboratory equipment.
Why Choose Cylance for IoT and Embedded Systems?
Holistic Device Security
Hackers attack remotely and when they have physical control of a device. Go beyond basic analysis, consider the entire ecosystem, supporting systems, credential storage schemes, and data encryption.
Highly Skilled Consultants
Cylance possess industry-leading world-renowned expertise and thought leadership. Get their deep understanding of embedded devices and network infrastructure working for your organization.
Proper Safeguards
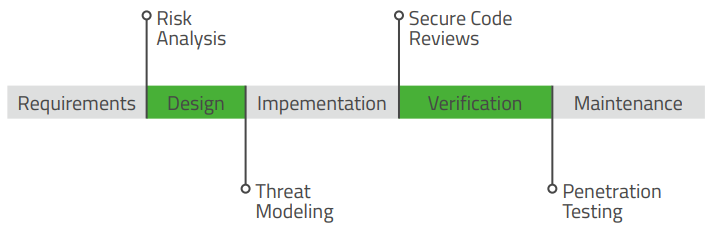
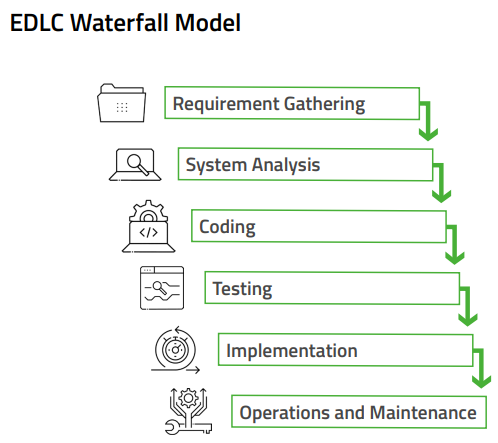
The best time to address device weaknesses is during the development lifecycle – to reduce risk of device failure and liability exposure. We help their clients to establish and adhere to industry best practices.
Fact Driven Remediation Strategy
We provide comprehensive reports and documented results to client stakeholders, including a strategic remediation roadmap to satisfy operational, tactical and governance requirements.
Additional Services for Added Insight
Med Secure Assessment Framework (MSAF)
Evaluate the current maturity of clinical information security programs and their impact on security and risk.
Secure Your Infrastructure With Facilisafe
Engage a single risk assessment that considers industrial control systems, medical devices and enterprise security.
Threat Modeling With Red Team Services
Initiate an assessment of a software system’s security risks and threats that have the greatest potential to impact an application.
Med Secure Assessment Framework (MSAF):
Organizations of all sizes need to quickly gauge the maturity of their information security program as it relates to clinical systems. Cylance’s MSAF (pronounced em-safe) focuses on allowing an organization to quantify the security risk non-traditional connected assets, such as medical devices, pose to their patients and computing environments.
How MSAF helps your organization
MSAF gauges the current maturity of the organization’s clinical information security program and its impacts on security and risk. The framework helps identify what processes, procedures, documents and technical controls should be put in place to help advance the organization further down the maturity roadmap
 How you use MSAF
How you use MSAF
- The Assessment Phase
MSAF is built using a combination of controls from ISO 27002, COBIT, NIST and industry best practices. We have distilled those controls and practices down to an easily utilized self-assessment questionnaire. This self-assessment questionnaire is used internally to assist the organization benchmark progress throughout the roadmap. Cylance uses an expanded version of the selfassessment questionnaire to help more accurately align your organization to the maturity roadmap. - The Alignment Phase
Cylance uses the self-assessment questionnaire and the data points gathered from the assessment phase to begin aligning your clinical information security program goals to the MSAF roadmap. This roadmap provides gates to measure program maturity as well as complementary functions your program should be able to provide internally as your organization matures. Examples of these include vendor disclosure programs, medical device testing, clinical vulnerability management, incident response, forensic functions and more. - The Audit Phase
The final phase of MSAF is to audit and benchmark progress along the roadmap for your organization. The audits provided by Cylance periodically throughout the year can help ensure your organization is meeting its clinical security goals as it moves toward maturity. Steady and managed growth of a clinical security program is essential.
MSAF and Medical Device Testing
One of the most critical parts of a mature clinical security program is a medical device testing program. These programs are used by organizations of all sizes to determine security and patient risk posed by the multiple forms of clinical systems within their environment. Cylance offers a full range of services meant to complement MSAF such as medical device reverse engineering, exploit development, testing education, vendor coordination and vulnerability management.
Download the Cylance ICS Assessment Datasheet (.PDF)
Medical Device Security Assessment:
Secure and Protect Patient Care Systems
The capabilities of modern medical devices continue to radically transform patient care, but also can present a danger to patients through ever-present cyber threats. For years, security researchers have been uncovering security flaws in medical devices, raising concerns of tampering. All medical devices that use software and are connected to networks have vulnerabilities which can be proactively protected against while others require vigilant monitoring and timely remediation. Better patient care is the goal for all healthcare institutions.
Cylance Consulting’s Medical Device Security Assessment helps medical device manufacturers and healthcare organizations to better secure and protect patient care equipment and systems from cyber attacks. Our dedicated team of IoT and Embedded Systems experts helps to assess vulnerabilities and develop a plan for responding to them, starting with the design phase.
Benefits
- Identify potential threats to networked medical devices
- Ensure proper safeguards are in place to reduce the risk to patients due to a cyber attack
- Limit medical device access to only trusted users
- Protect individual components from exploitation
- Maintain a device’s critical functionality
Service Overview
Cylance Consulting will perform a black-box assessment of the medical device, including both manual and automated testing techniques. The in-depth analysis of embedded vulnerabilities will be covered at a technical level, focusing on the common vulnerability types that can be found in embedded applications.
Specific areas of the assessment include:
- Data Flow Analysis — Trace data points from input to output, including storage and destruction, to identify potential weaknesses
- Control Flow Analysis — Identify threats by stepping through logical conditions and identify all possible paths through which code may traverse
- Structural Analysis — Evaluate the security of high-level architecture at multiple tiers and the composition of the application and its subsystems, including physical deployment characteristics
- Configuration Analysis — Assess the security configuration of all relevant components to identify vulnerabilities
- Semantic Analysis — Analyze the code base within the application’s context to identify vulnerabilities unique to the application and environment
Deliverables
As part of the security assessment, Cylance Consulting will provide a comprehensive report detailing:
- • Our findings with any potential indicators of compromise
- A graphical summary of testing results
- A strategic remediation roadmap, including:
- Finding name with details
- Vulnerable host/IP
- Vulnerability severity
- Detailed recommendations
- Screen shots
- Assigned owner and remediation priority
Improve the security posture of your healthcare ecosystem. Contact Cylance Consulting or your technology provider to discuss your needs.
Download the Cylance Med Device Security Assessment Datasheet (.PDF)
Embedded System Security Assessment:
Secure and Protect Embedded Devices
Embedded products are expanding our ability to communicate and share information. The rapid growth in the interconnectedness of these devices has also been accompanied by an increase in security threats. Cyber criminals can perform a DDoS attack through the backdoor of these IoT devices. Developers of embedded devices need to consider security issues at every layer – from hardware platforms, virtualization technologies, operating systems, network and communications middleware, and the applications required to support device functionality.
Cylance Consulting’s Embedded System Security Assessment helps development teams cut costs and time frames while decreasing overall security risks. Cylance’s dedicated team of IoT and Embedded Systems experts helps to assess vulnerabilities and develop a plan for responding to them, starting with the design phase.
Benefits
- Identify potential security risks in embedded devices
- Ensure proper safeguards are in place to reduce the risk of device failure due to a cyber attack
- Reduce operational costs by discovering and addressing device weaknesses during the development lifecycle
- Improve customer confidence by improving device robustness and reliability
- Reduce liability exposure by adhering to industry best practices for risk mitigation
Service Overview
Cylance Consulting will perform a black-box assessment of the embedded device, including both manual and automated testing techniques. The in-depth analysis of embedded vulnerabilities will be covered at a technical level, focusing on the common vulnerability types that can be found in embedded applications.
Specific areas of the assessment include:
- Data Flow Analysis — Trace data points from input to output, including storage and destruction, to identify potential weaknesses
- Control Flow Analysis — Identify threats by stepping through logical conditions and identify all possible paths through which code may traverse
- Structural Analysis — Evaluate the security of high-level architecture at multiple-tiers and the composition of the application and its subsystems, including physical deployment characteristics
- Configure Analysis — Assess the security configuration of all relevant components to identify vulnerabilities
- Semantic Analysis — Analyze the code base within the application’s context to identify vulnerabilities unique to the application and environment
The analysis will allow organizations to gain full-spectrum visibility into their security ecosystem with the objective of moving the environment into a state of prevention.
Deliverables
As part of the security assessment, Cylance Consulting will provide a comprehensive report detailing:
- Our findings with any potential indicators of compromise
- Graphical summary of testing results
- A strategic remediation roadmap, including:
- Operational requirements
- Tactical requirements
- Governance requirements
Address security challenges in your embedded products before they become pervasive security problems. Contact Cylance Consulting or your technology provider to discuss your needs.
Download the Cylance Embedded Security Assessment Datasheet (.PDF)
